Easy Steps
for All Users
Step 1
Register
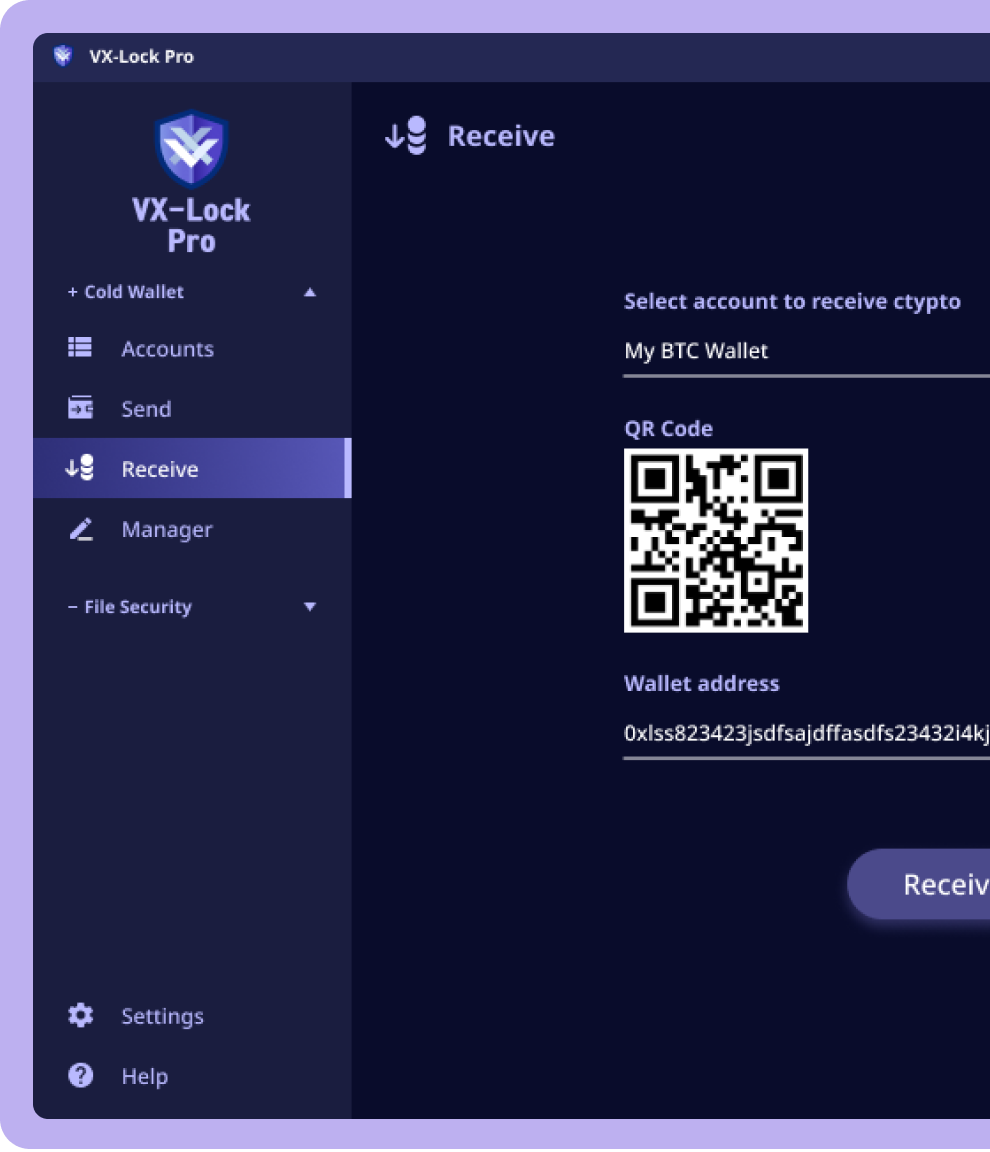
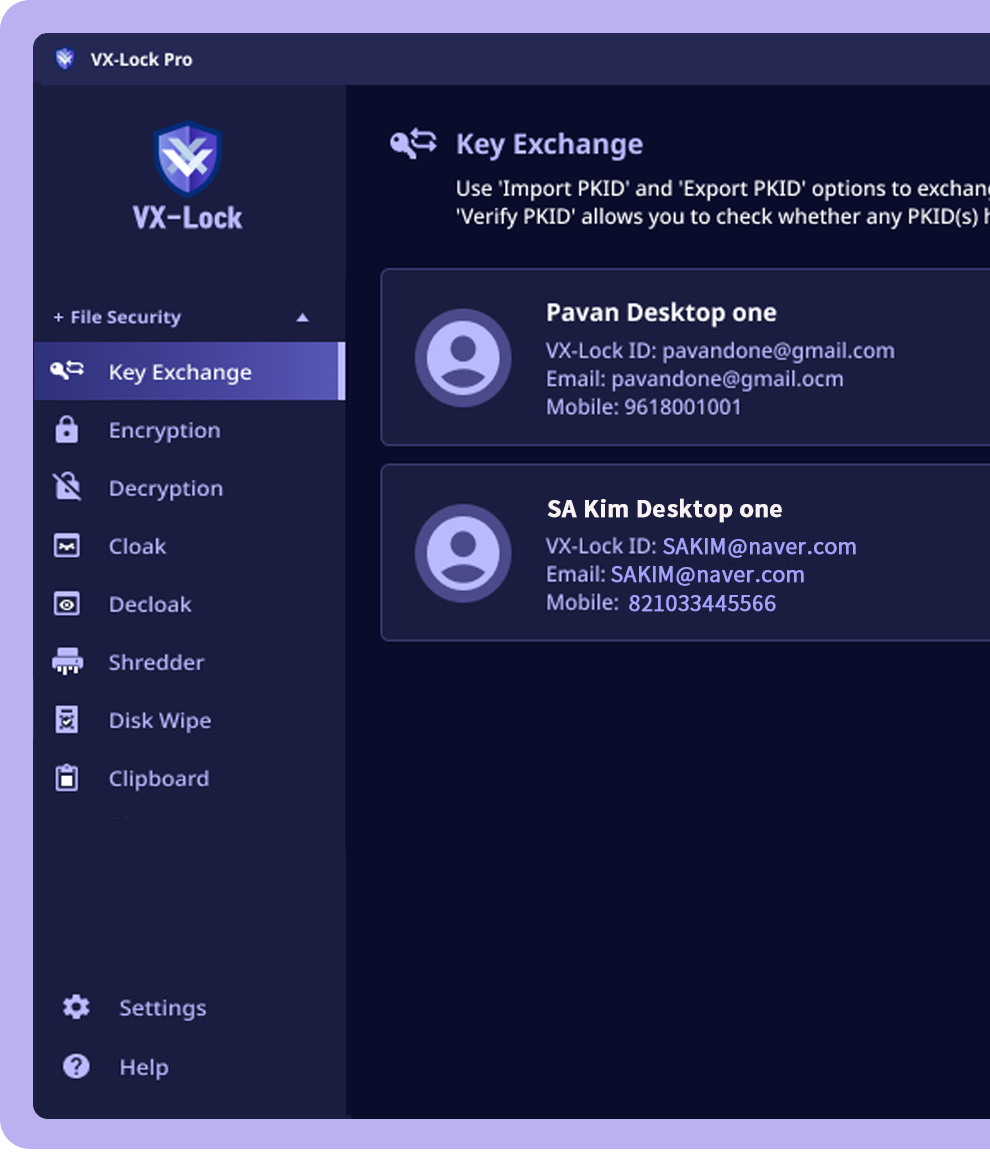
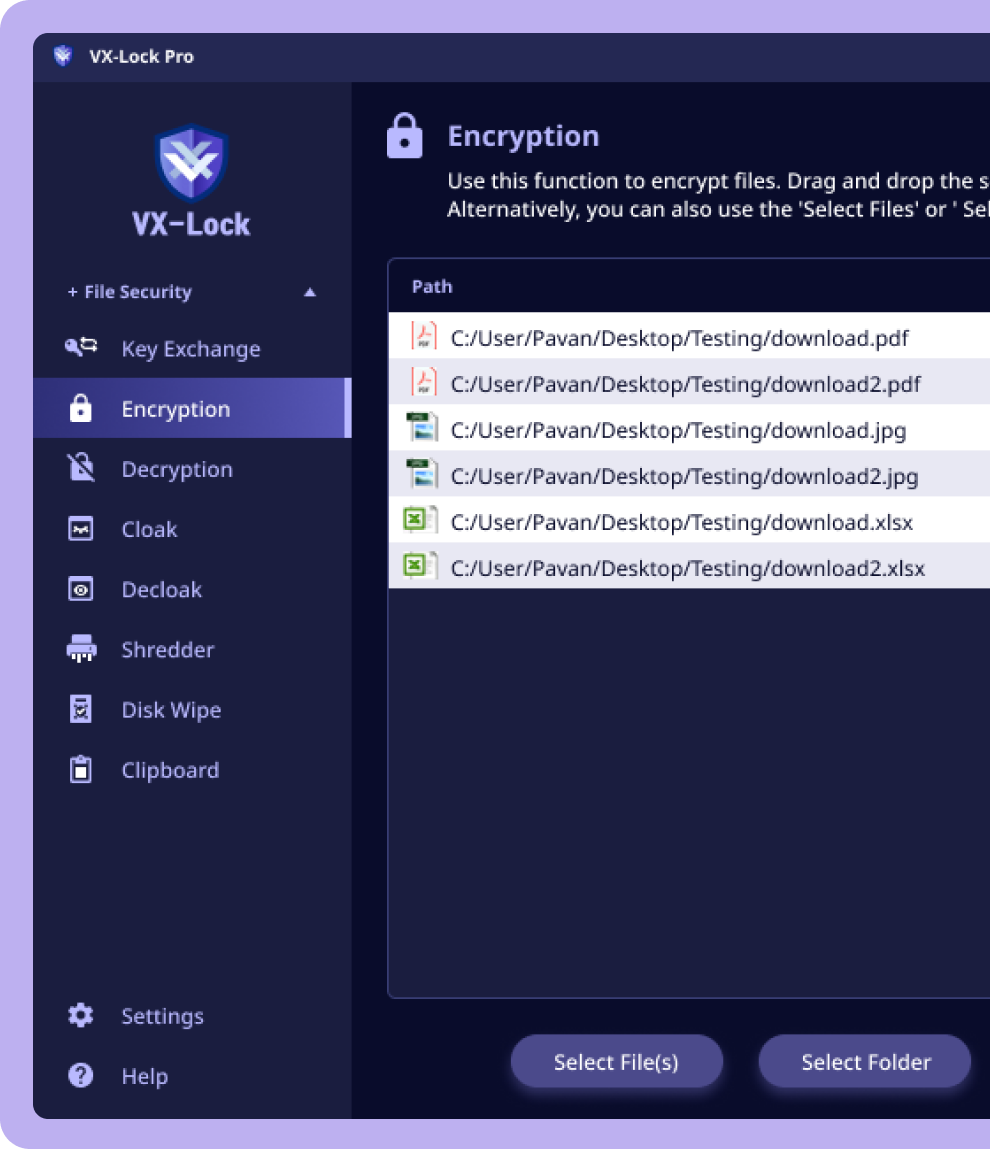
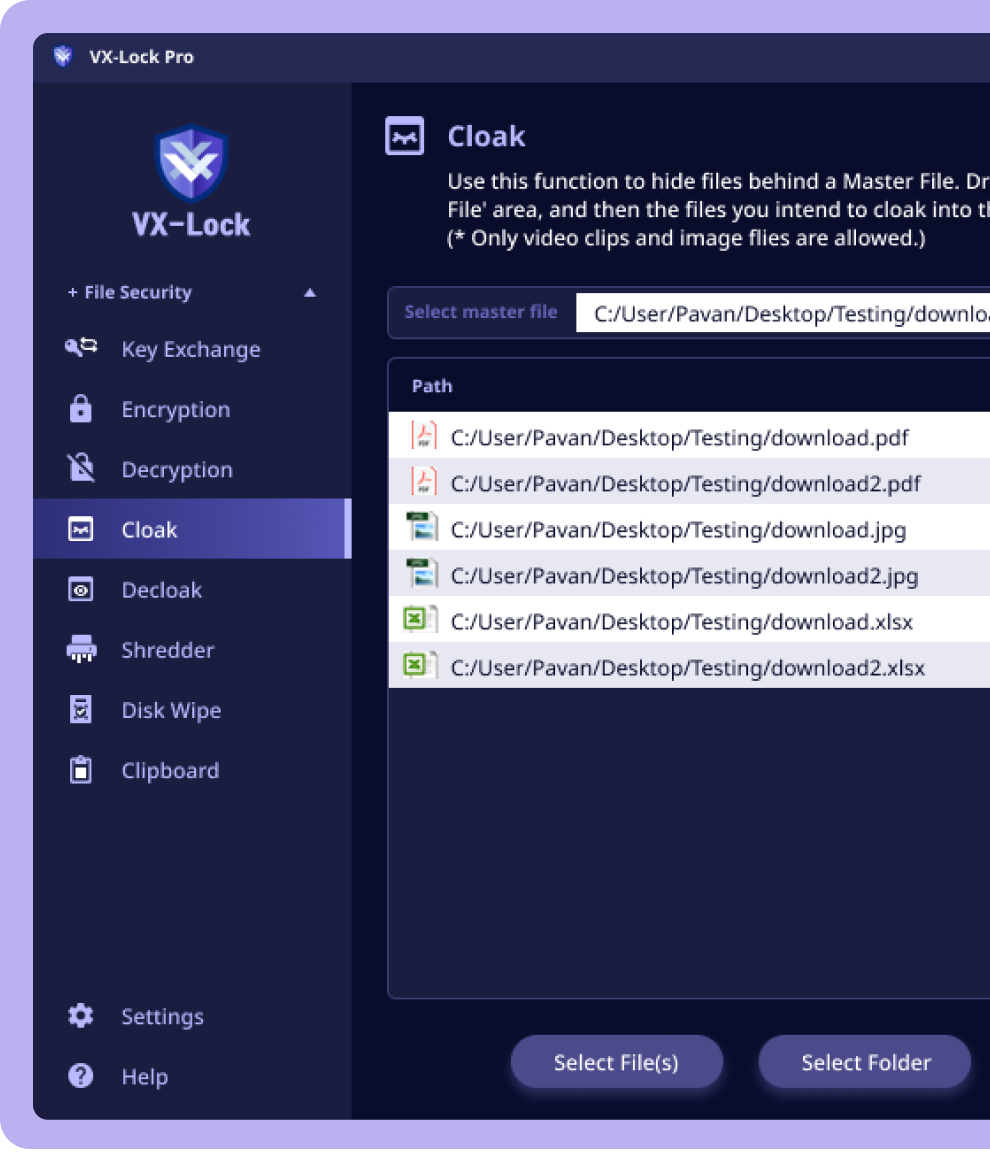
Register your Crypto or NFT Asset accounts for secure management. Add your account securely whenever you achieve new Crypto or NFT Assets.
Step 2
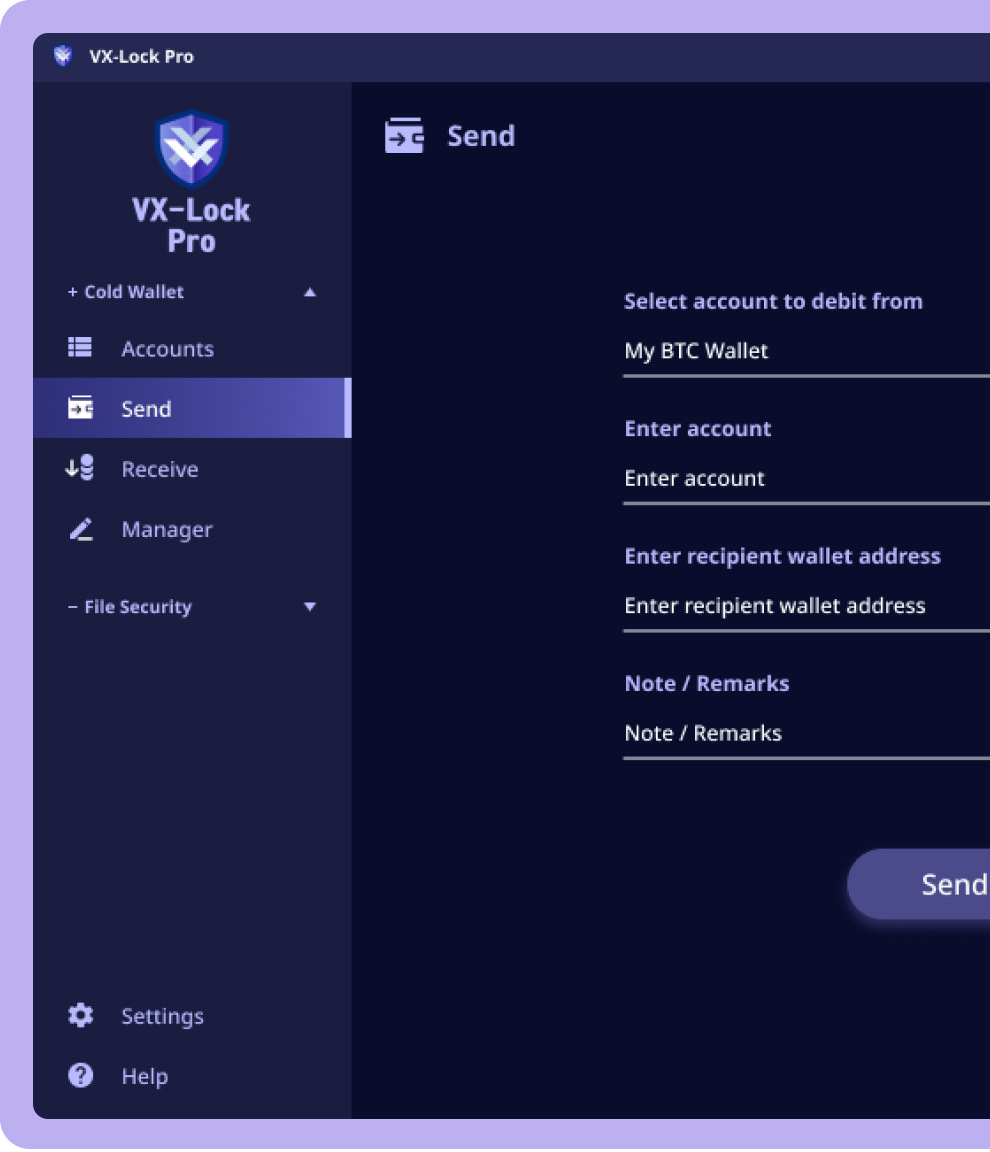
Send
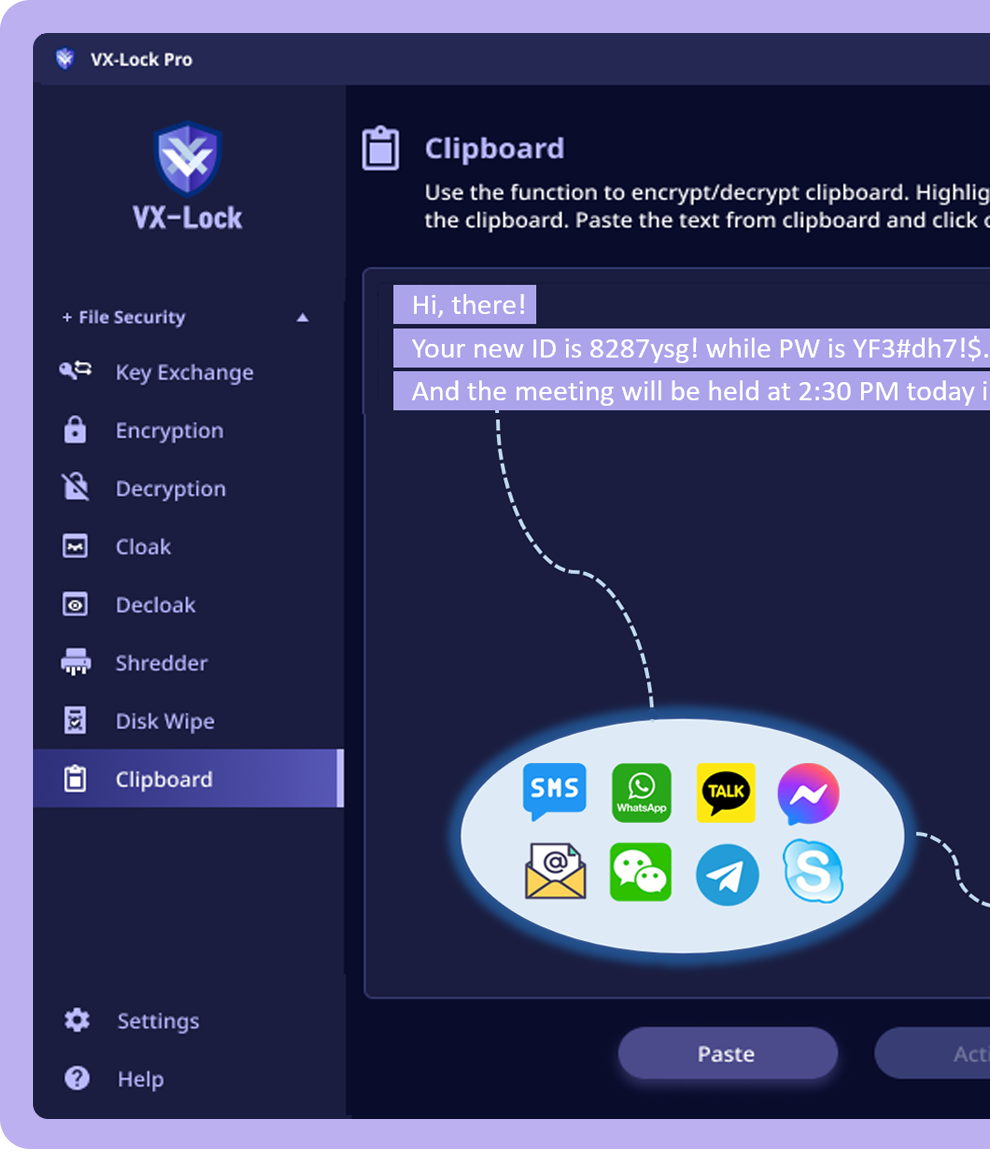
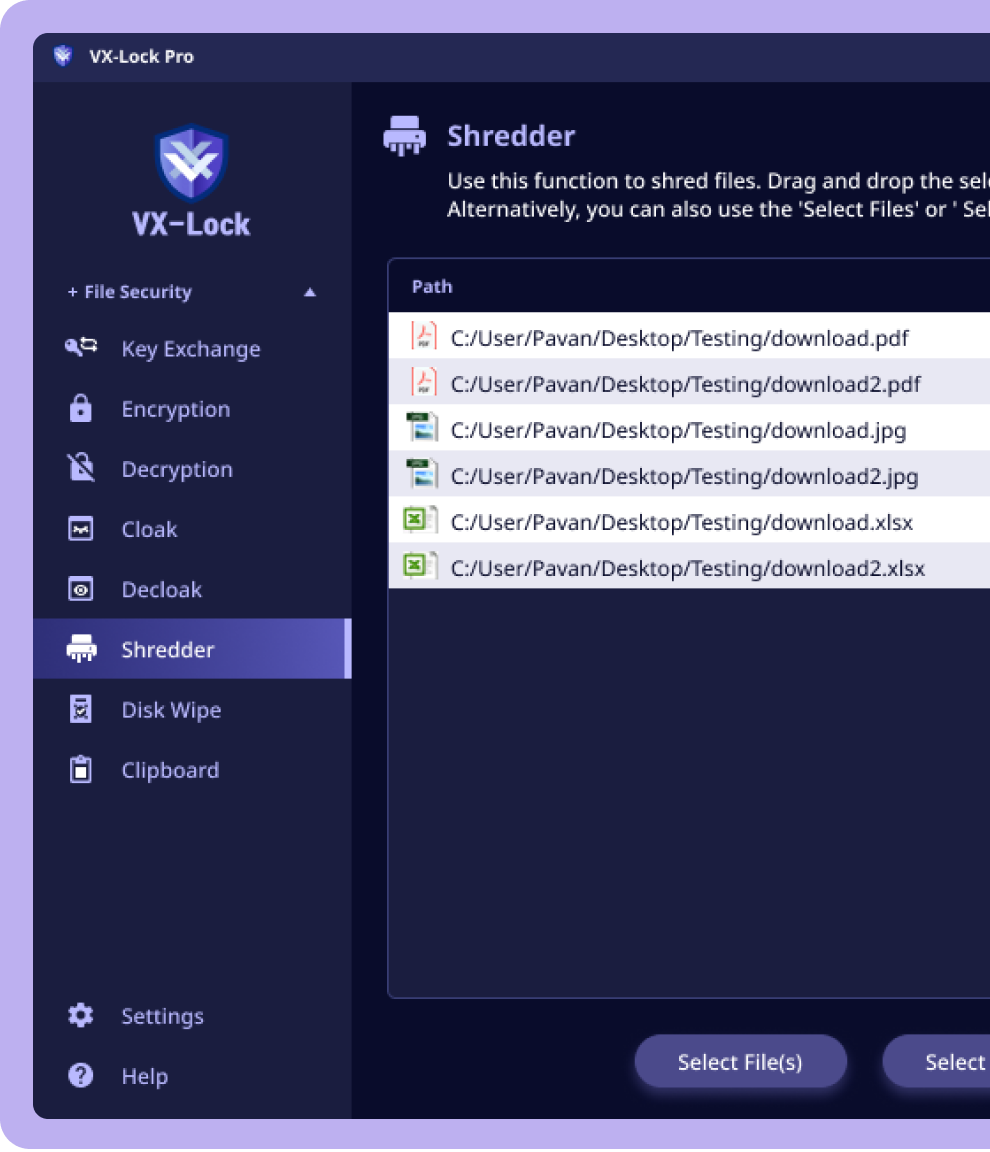
Send your Crypto & NFT Assets securely to other accounts. Keep the rest of Assets absolutely securely utilizing strongest encryption algorithms.